Definition Of Data Integrity In Network Security

Viruses spam network intrusions and denial of service attacks are just a few examples of the threats in existence today that can adversely affect a company s network.
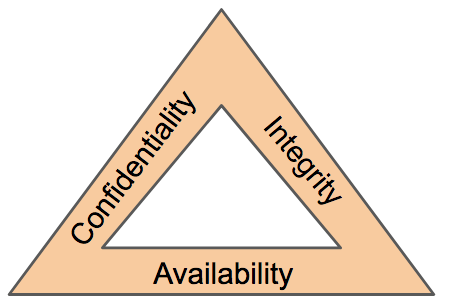
Definition of data integrity in network security. That said data integrity is a desired result of data security but the term data integrity refers only to the validity and accuracy of data rather than the act of protecting data. This definition explains what the confidentiality integrity and availability cia model is and how it guides policies designed to protect data security. Confidentiality integrity and availability often known as the cia triad are the building blocks of information security. Data integrity and data security are two important aspects of making sure that data is useable by its.
Data integrity vs data security data are the most important asset to any organization. Data integrity must be imposed when sending data. Any attack on an information system will compromise one two or all three of these components. Integrity in the context of computer systems refers to methods of ensuring that data is real accurate and safeguarded from unauthorized user modification.
Data integrity is a more broad application of policies and solutions to keep data pure and unmodified. But it also provides for measures to record maintain and preserve data in its original condition. Data integrity contains guidelines for data retention specifying or guaranteeing the length of time data can be retained in a particular database. This post explains each term with examples.
Search server virtualization how to evaluate vdi hardware requirements vdi has specific hardware needs that servers. To achieve data integrity these rules are consistently and routinely applied to all data entering the system and any relaxation of enforcement could cause errors in the data. Data integrity in the context of networking refers to the overall completeness accuracy and consistency of data. Integrity in terms of data and network security is the assurance that information can only be accessed and modified by those authorized to do so.
Confidentiality integrity and availability also known as the cia triad is a model designed to guide policies for. Therefore it must be made sure that data is valid and secure all the time.